- Best for server protection: Symantec Endpoint Protection
- Best for comprehensive endpoint security: Harmony Endpoint Protection
- Best for endpoint visibility: CrowdStrike Falcon
- Best for intelligence-led business protection: Trellix Endpoint Security
- Best for port monitoring: Trend Micro Advanced Threat Protection
- Best for identity threat detection: Cortex XDR
- Best for small and mid-sized businesses: ESET Endpoint Security
- Best for new users: Sophos Intercept X
Cyber threats have taken some advanced posturing and so should the tools devised to protect systems against them. Leading Advanced Threat Protection (ATP) tools refer to dynamic endpoint protection and cyber defense solutions that use both AI and ML technologies to better recognize and defend against sophisticated ransomware, phishing threats and other advanced cyberattacks. They feature capabilities such as real-time endpoint detection and response, zero-day threat protection, AI/ML-powered threat intelligence and other advanced threat protection techniques.
In this article, we will discuss the best ATP tools and solutions in 2024.
Top advanced threat protection tools and solutions: Compared
| Real-time Endpoint Detection and Response (EDR) | Machine Learning and AI | MDR capabilities | On-premises, Cloud-based and Hybrid deployment | User and Entity Behavior Analytics (UEBA) | Pricing | |
|---|---|---|---|---|---|---|
| Symantec Endpoint Protection | Yes | Yes | No | Yes | Yes | Contact vendor for pricing. |
| Harmony Endpoint Protection | Yes | Yes | Yes | Yes | Yes | Contact vendor for pricing. |
| CrowdStrike Falcon | Yes | Yes | Limited | Cloud-based and on-premise | Yes | Starts at $4.99/device/month. |
| Trellix Endpoint | Yes | Yes | Yes | Yes | Yes | Contact vendor for pricing. |
| Trend Micro | Yes | Yes | Yes | Yes | Yes | Starts at $37.75/ user/year. |
| Cortex XDR | Yes | Yes | No | Yes | Yes | Contact vendor for pricing. |
| ESET Endpoint | Yes | Yes | Yes | Yes | Yes | Starts at $211/year. |
| Sophos Intercept X | Yes | Yes | Yes | Yes | Yes | Contact vendor for pricing. |
Best advanced threat protection solutions
Here’s an in-depth look at the leading ATP solutions, their features, pricing, pros and cons.
Symantec Endpoint Protection: Best for server protection

Developed by Broadcom, Symantec Endpoint Security is an advanced security platform for endpoint security, server security and endpoint management. It is equipped with advanced threat-prevention capabilities for both traditional endpoints and mobile devices.
The solution integrates cloud-based protection with AI-powered security management in a single agent/console design. It features a range of functionalities, including attack surface reduction, attack prevention, breach prevention and Endpoint Detection and Response (EDR) through a single agent.
One of its standout features is adaptive EDR, which offers insights into the threat landscape, custom behavioral insights and recommendations. It also includes Targeted Attack Analytics and Threat Hunter, which utilize machine learning across telemetry from all Symantec Endpoint customers to detect new attacks and provide recommended actions.
Why we chose Symantec Endpoint Protection
We chose Symantec Endpoint Security because it offers complete server protection, monitoring and workload micro-segmentation for both private cloud and physical on-premises data center environments.
Pricing
Contact the vendor for a quote.
Features
- Adaptive protection.
- Centralized cloud management.
- Targeted attack analytics.
- Firewall and intrusion prevention.
- Automated threat hunting.
Pros
- Enterprise-wide breach protection.
- Real-time endpoint visibility and behavior.
- Supports on-premises, cloud and hybrid model deployments.
- AI guidance for policy creation and deployment.
- Uses a single agent for easy endpoint management.
Cons
- Managing multiple endpoints on a single agent can be overwhelming.
Harmony Endpoint Protection: Best for comprehensive endpoint security

Formerly known as SandBlast Agent, Harmony EndPoint Protection automates tasks related to threat detection, investigation and remediation. Noteworthy features include protection against ransomware, phishing, malware, fileless attacks and credential theft. It also includes a unified agent for EPP, EDR, VPN, NGAV, data and web-browsing protection, as well as credential, behavioral, email and URL protection.
The solution is compatible with Windows, macOS and Linux and can be run either on-premises, hybrid or using a cloud service. With six different Harmony Endpoint packages, the solution can be used for small businesses and large enterprises.
Why we chose Harmony Endpoint Protection
Harmony Endpoint Protection made it to our list due to its comprehensive approach to endpoint threat detection and remediation, which is ideal for any size business.
Pricing
This solution features three main subscription tiers: Basic, Advanced and Complete. A 30-day free trial is available for up to 100 endpoints. For pricing information, contact the vendor.
Features
- Host firewall and application control.
- Centralized Management.
- Threat hunting.
- Content Disarm and Reconstruction (CDR) across email and web.
- Zero-day Phishing site protection.
Pros
- Forensics collection and automated reports.
- Supports remote access VPN.
- Host and media encryption.
- Web protection.
- Offers forensics report.
Cons
- The on-premises server comes at an additional cost.
CrowdStrike Falcon: Best for endpoint visibility

CrowdStrike Falcon is a cloud-native platform that provides AI-powered threat protection across various risk points, including endpoints, workloads, data and identity. The platform is designed for scalability and ease of management and caters to enterprise and small business users.
The platform’s key features include Threat Graph and Falcon Fusion. Threat Graph offers immediate access to actionable data and user-friendly dashboards for advanced workflows and visualizations. Falcon Fusion combines artificial intelligence and automation to speed up incident detection and response. CrowdStrike Falcon uses real-time attack indicators, threat intelligence and enriched telemetry data for threat detection, automated protection and remediation, threat hunting and observability.
Why we chose CrowdStrike Falcon
We chose CrowdStrike Falcon due to its unified platform and approach to threat detection and remediation, which facilitate comprehensive visibility.
Pricing
This solution has plans for small business and enterprise use.
Small business
- Falcon Go: $4.99/month.
- Falcon Pro: $8.33/month.
Both require a minimum of five devices and a one-year contract.
Enterprise
- Falcon Pro: $499.95/year for a minimum of five devices.
- Falcon Enterprise: $924.95/year for a minimum of five devices.
Falcon Elite: Contact Falcon for pricing.
Features
- Falcon USB Device Control.
- Lightweight installation.
- Endpoint Detection and Response (EDR) Capabilities.
- Firewall management.
Pros
- Visibility with USB device control.
- Ease of deployment and updates.
- Comprehensive pricing.
- Supports an antivirus.
- Real-time visibility with Threat Graph.
Cons
- As a cloud-native platform, there might be concerns about data privacy and security.
- Falcon Insight XDR comes as an add-on.
Trellix Endpoint Security: Best for intelligence-led business protection

Trellix Endpoint Security, known for its threat intelligence-driven approach, uses a combination of machine learning and behavioral analysis to detect and block threats. It employs dynamic machine learning, artificial intelligence and multi-vector virtual execution (MVX) for capturing and confirming zero-day and advanced threat variants. Its XDR architecture is designed to adapt to the speed of threat actors and deliver advanced cyber threat intelligence.
The solution also features Universal Access Control protections, host remediation, process tracking and near real-time IoC capabilities. Trellix Endpoint Security is compatible with Windows, MacOS and Linux. It’s available in multiple deployment options—as a standalone hardware appliance, a virtual appliance or through cloud deployment.
Why we chose Trellix Endpoint Security
We chose Trellix Endpoint Security for its emphasis on intelligence-driven protection, which offers a more proactive defense than traditional endpoint security.
Pricing
Contact the vendor for a quote. A demo is also available on request.
Features
- Advanced threat intelligence integration and analytics.
- Centralized cloud management.
- Behavioral analysis and machine learning.
- Endpoint detection and response (EDR) Capabilities.
- Modular design for scalability.
Pros
- SecOps modernization.
- Supports extra modules for enhanced alerts.
- Unified dashboard.
- Proactive risk management.
- Dynamic threat protection.
Cons
- Multiple agents and modules can be confusing.
- Premium customer service comes at an extra cost.
Trend Micro Advanced Threat Protection: Best for port monitoring

Trend Micro Advanced Threat Protection solution provides real-time protection against advanced threats as well as helps enterprises carry out advanced sandbox analysis, threat sharing and analytics. The solution includes its Deep Discovery Inspector, which monitors all ports and over 105 different network protocols to discover advanced threats.
Additional features include Threat Sharing and Analytics, which enhance threat visibility and facilitate threat detection through standards-based sharing and event correlation. Trend Micro also features a managed XDR for alert monitoring, prioritization, threat investigation and threat hunting. These features collectively provide comprehensive network protection, advanced sandbox analysis and threat sharing and analytics.
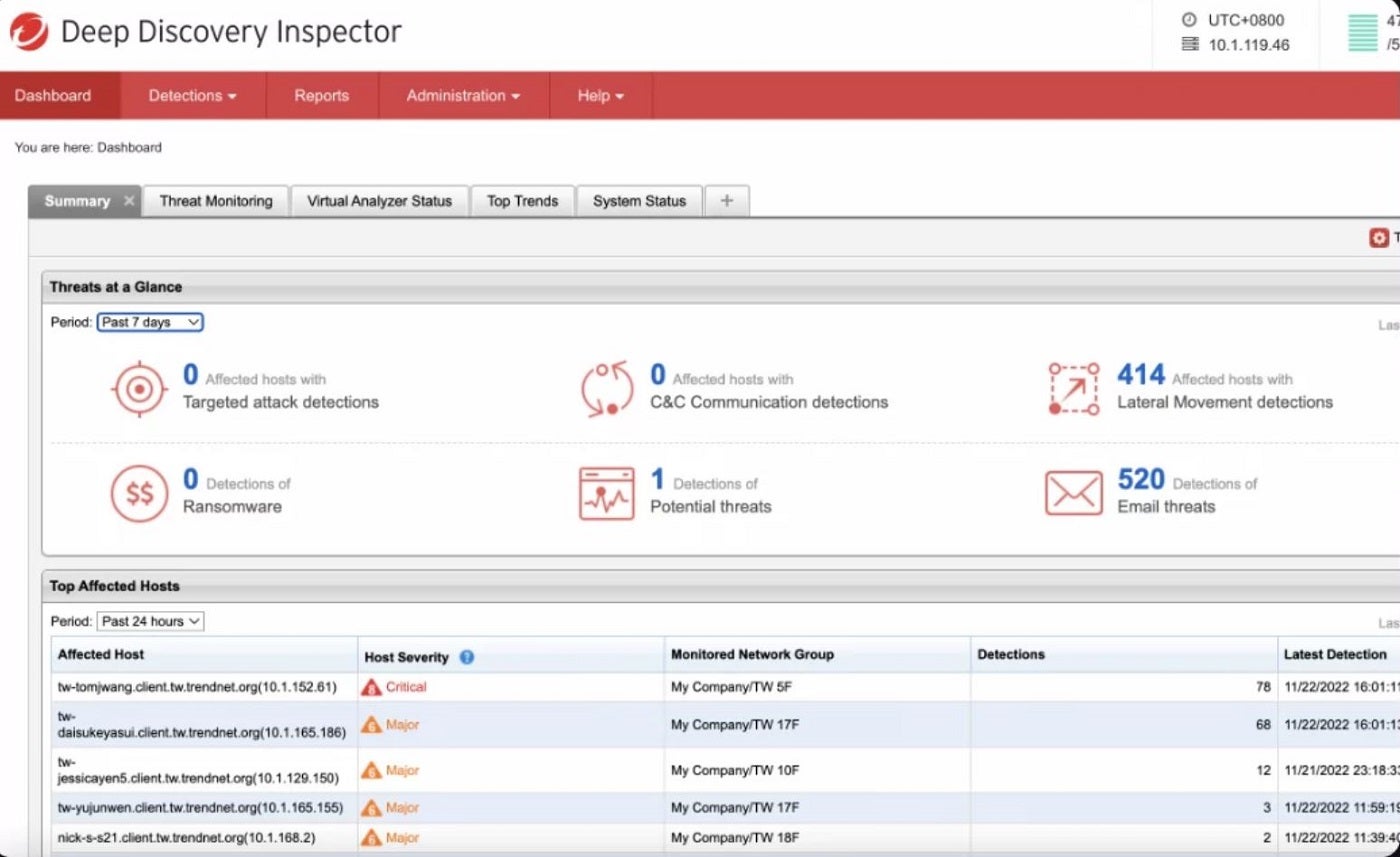
Why we chose Trend Micro
This tool made it to our list for its special attention to port monitoring across multiple network protocols.
Pricing
Trend Micro has four plans, and all offer a free 30-day trial period.
- Worry-free Service: Starts at $37.75/year per user.
- Worry-free Service Advanced: Starts at $59.87/year per user.
- XDR service: Contact the vendor for a quote.
- Co-managed XDR services: Contact the vendor for a quote.
Features
- Threat sharing and analytics.
- Endpoint and email security.
- Single-agent EDR across email and endpoints.
- Automated root cause analysis and actions against threats.
- Endpoints monitor enabled by firewalls and IPSs.
Pros
- Cross-customer detection, investigation and response.
- Cloud sandboxing for advanced threat detection.
- 24/7 critical alerting and monitoring.
- Monitors over 105 different network ports.
- Utilizes census and safe listing to minimize false positives.
Cons
- Endpoint agent names cannot be renamed after being assigned.
- Limited features on some editions.
Cortex XDR: Best for identity threat detection

Palo Alto’s Cortex XDR uses Next Gen Antivirus (NGAV), host firewall, disk encryption, USB device control and MITRE ATT&CK framework to ensure strong endpoint security. It analyzes data from various sources to prevent sophisticated attacks and is designed to keep devices safe whether they are online or offline.
With additional features like Zero Trust Network Access, Cloud Security, Remote Browser Isolation, Data Center Security and Intrusion Detection, Cortex XDR covers a wider spectrum of advanced threats. Some of the threats include advanced malware, evasive threats, phishing and IoT-based threats.
Enhanced by the eXtended Threat Hunting (XTH) data module, the platform helps security teams quickly detect and prevent threats. As an extra layer of security, its Cortex XSIAM and XDR have an identity threat detection and response module to prevent identity threats like hacked accounts and insider threats.
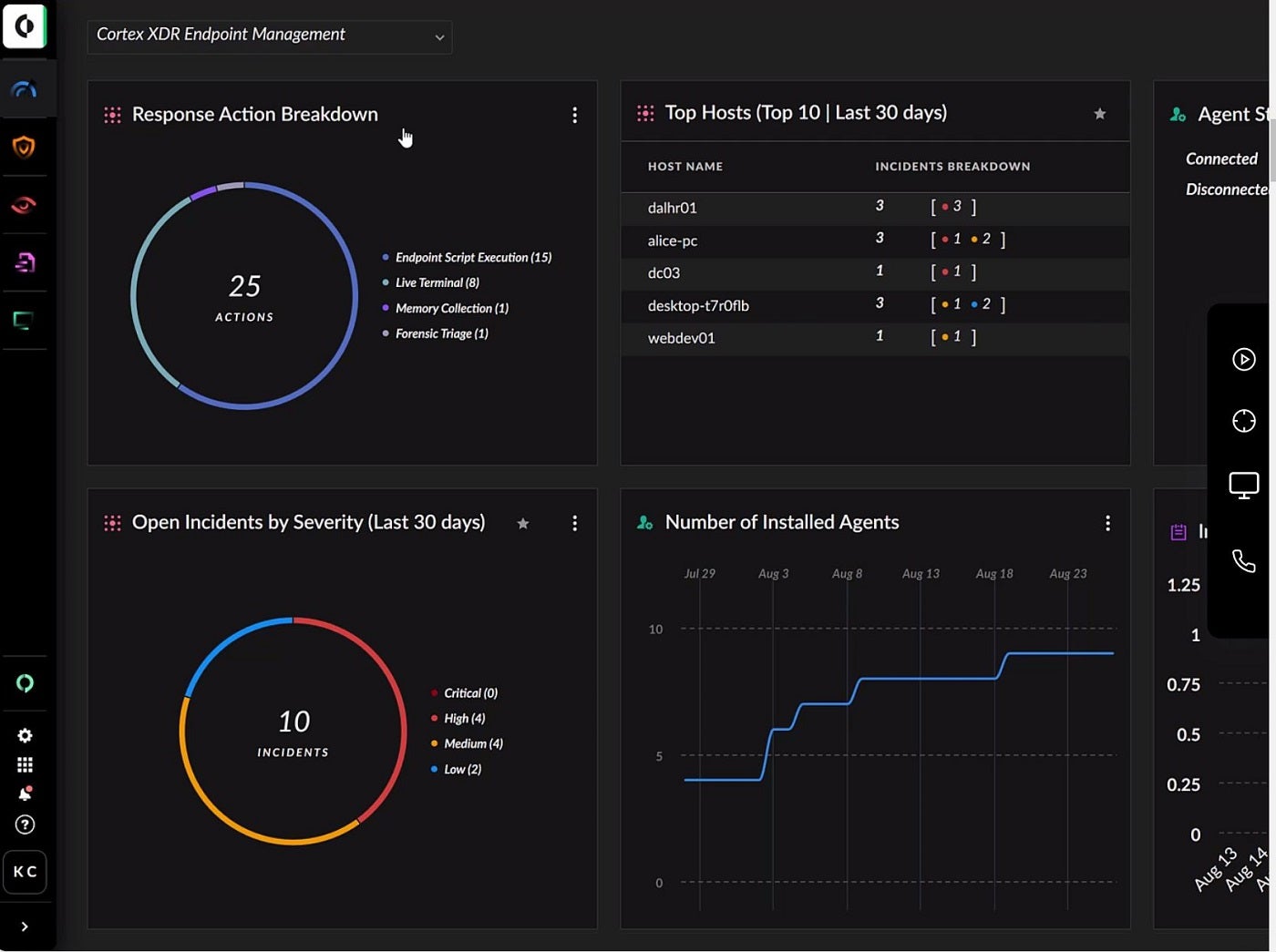
Why we chose Cortex XDR
We chose Cortex XDR because of its blend of identity threat detection, Next Gen Antivirus (NGAV) and advanced endpoint security.
Pricing
Contact the vendor for a quote
Features
- 360-degree user view.
- ATT&CK mapping.
- Incident management.
- Behavioral analytics.
- Network detection and response across all devices.
Pros
- Offer deep visibility.
- ML-driven threat detection.
- Full visibility to eliminate blind spots.
- Offers a 30-day free trial.
Cons
- No eXtended Threat Hunting for its XDR Prevent plan.
- Requires a steep learning curve to navigate its advanced features.
ESET Endpoint Security: Best for small and mid-sized businesses

ESET Endpoint Security is another big name in the advanced threat protection landscape. Offered as a cloud-based and on-premises advanced security solution, ESET is designed to protect home and company PCs, file servers and mobile devices from viruses, brute force attacks and other attack vectors. Through a combination of cloud-powered threat hunting and machine learning, it prevents, detects and automatically responds to malware threats.
In addition, ESET Endpoint Security includes a software firewall and a Host-based Intrusion Prevention System (HIPS) that uses a predefined set of rules to identify and stop dubious activities. It also offers web access and email client protections to catch and block malicious downloads and harmful web pages.
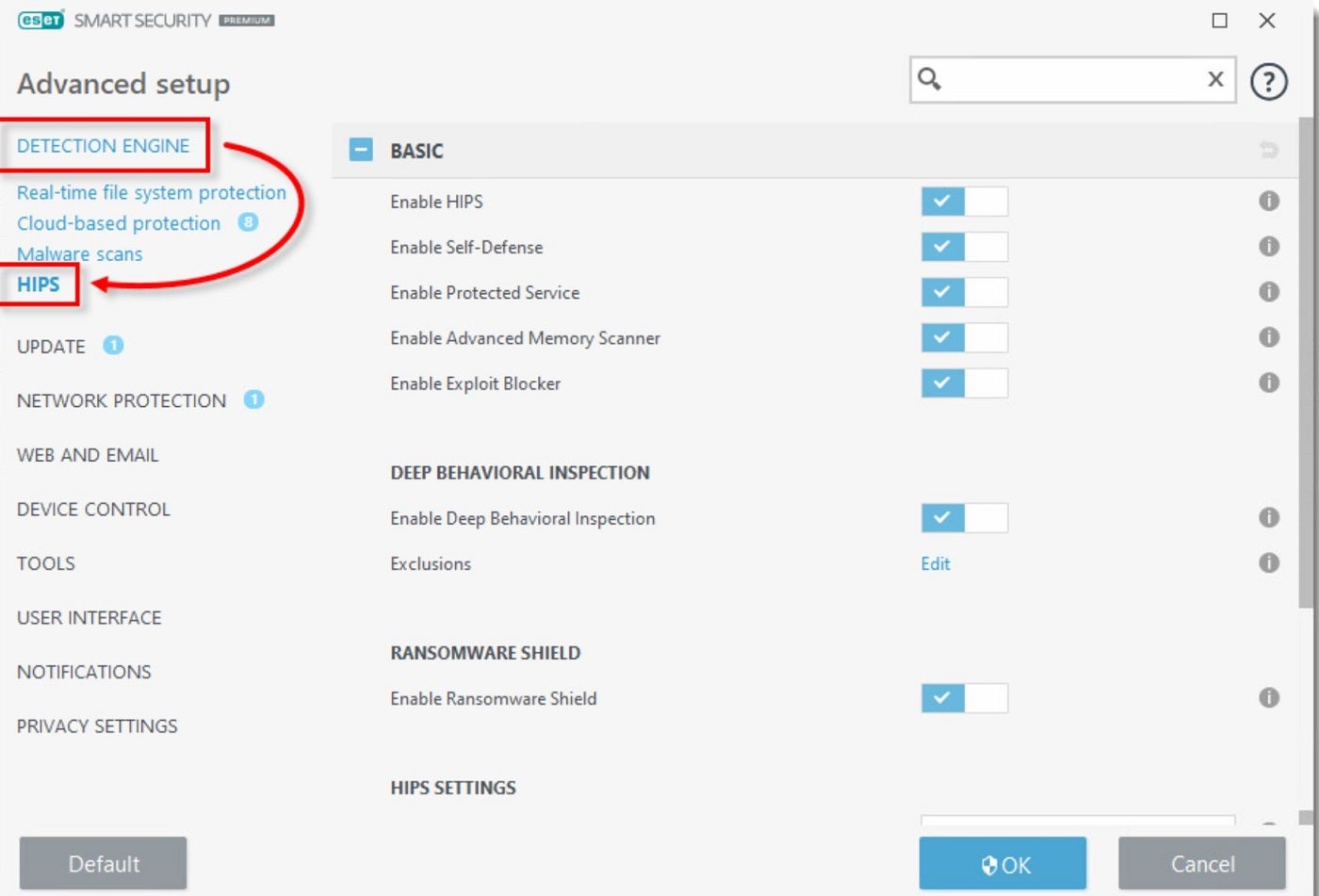
Why we chose ESET
ESET made it to our list following its multi-layered prevention-first approach to defense against ransomware, phishing and email threats. It’s also easy to manage, which is ideal for small and mid-scale businesses.
Pricing
There are four main plans (Protection Tiers) and six add-ons (Additional solutions), all billed annually. This pricing features their current discounted prices and their normal prices.
Protection Tiers
- Protect Entry: $211/year for five devices.
- Protect Advanced: $275/year for five devices.
- Protect Complete: $338.50/year for five devices.
- Protect Elite: Requires a minimum of 26 devices. Contact ESET for a quote.
Features
- Anti-exploit technology.
- Unified security management console.
- Centralized management.
- Enterprise-grade XDR.
- Hybrid deployment support.
Pros
- Easy to manage.
- Supports infection remediation.
- Ransomware detection and prevention.
- Compatible with multiple operating systems.
- Can either be on-premises or cloud.
Cons
- Integration with third-party tools can be difficult.
- Enterprise-grade XDR is only available to Protect Elite users.
Sophos Intercept X: Best for new users

Sophos Intercept X is an AI and ML-powered ATP solution designed to halt a wide range of attacks. It utilizes web, application and peripheral controls to minimize the attack surface and block common attack vectors. The software also features patented CryptoGuard technology, which detects and stops ransomware, including new variants and both local and remote ransomware attacks. Additionally, Intercept X enhances the basic protection available in Microsoft Windows by adding over 60 proprietary, pre-configured and tuned exploit mitigations.
Another key feature is its context-sensitive defenses that adapt in response to known and unknown threats. The solution also features Sophos Central, a cloud-based platform that makes it easy to set up and manage Sophos products. With recommended protection technologies enabled by default, new users can set things up without worrying about additional tuning.
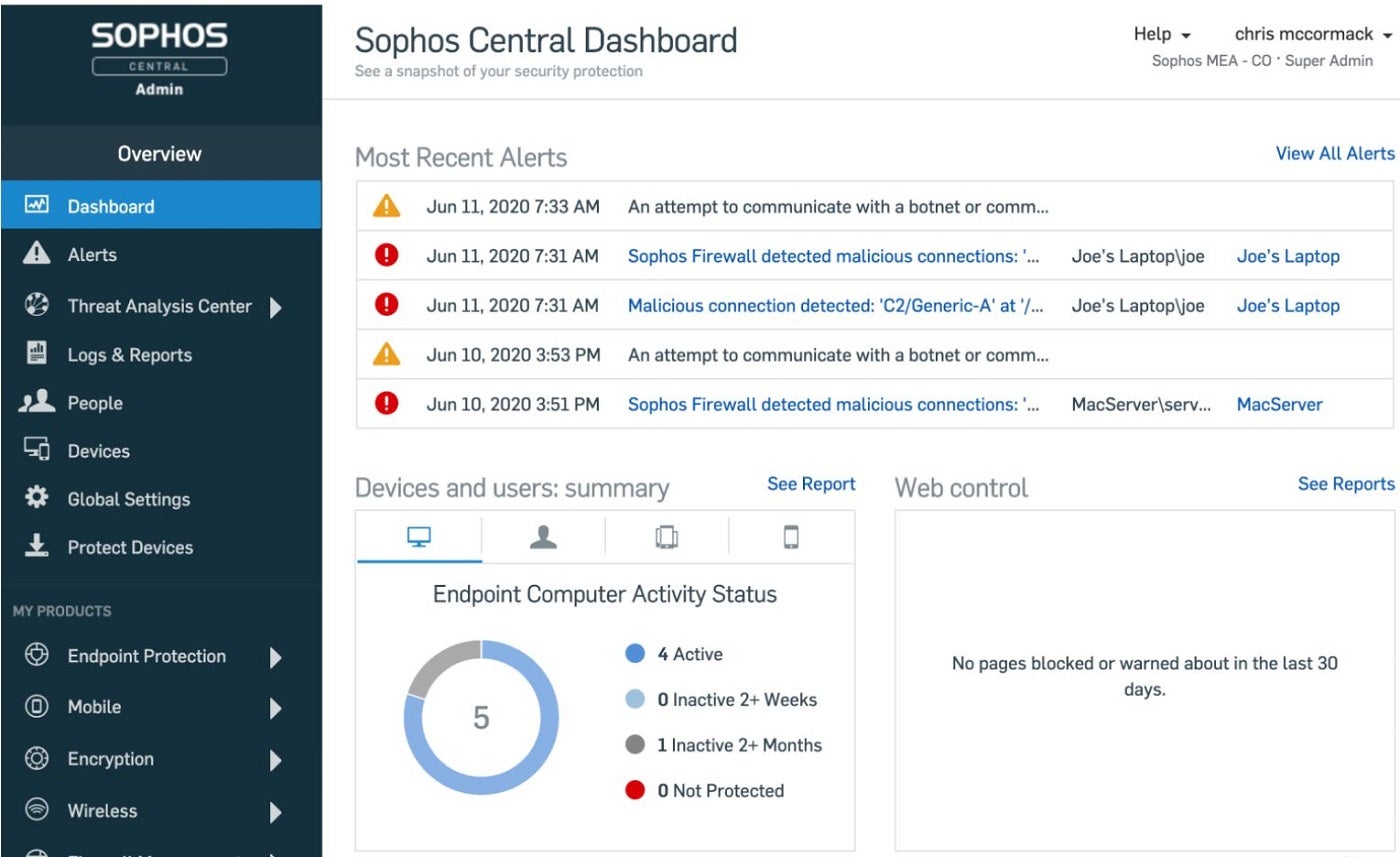
Why we chose Sophos Intercept X
This solution was picked due to its recommendation engine, which enables users to utilize the solution out of the box and without the need for extensive technical configurations.
Pricing
Sophos Intercept X comes with a 30-day free trial for its three plans: X Advanced, Advanced with XDR and Advanced with MDR Complete. For specific pricing, contact the vendor for a quote.
Features
- SQL querying protections.
- Cross-product querying.
- Human-led threat hunting and response features.
- Sophos Central web console.
- Sophos ZTNA with EDR and MDR.
Pros
- Easy to use.
- Effective in deploying and identifying drifts in security posture.
- Adaptive attack protection.
- Provides security alerts.
- Offers a 30-day free trial.
- Comprehensive account health check.
Cons
- Not compatible with some devices.
Key features of advanced threat protection software
To protect against ever-evolving cyber threats, advanced threat protection tools should come equipped with a few key features.
Behavioral analysis
Behavioral analysis includes establishing a baseline of the network’s normal behavior, employing anomaly detection through advanced algorithms and utilizing User and Entity Behavior Analytics (UEBA) to monitor and profile users or entities. Behavioral analysis is an important feature that enables ATP tools to understand and analyze system behavior and then flag any deviations that signify a potential threat.
Machine learning and AI
Machine learning and AI play a crucial role in advanced threat protection solutions. They help identify and predict threats by analyzing patterns in data. ML algorithms learn from historical cyber attack patterns and AI uses this information to predict and prevent future threats. This integration of machine learning and AI allows for real-time threat detection, rapid response and minimal system downtime, enhancing the overall security posture of an organization.
Threat intelligence integration
Incorporating threat intelligence ensures the constant update of the tool with the latest information on known and emerging threats. By utilizing up-to-date information on emerging threats, Advanced Threat Protection systems can make more informed decisions, correlate events and strengthen their overall security posture. Threat intelligence integration is important in keeping the network resilient to attacks and building a proactive defense against sophisticated threats.
Real-time endpoint detection and response (EDR)
Real-time EDR allows for continuous monitoring and immediate response at the endpoint level of a network. To achieve this, it employs real-time analysis of endpoint activities and identifies and responds to security incidents as quickly as possible. This immediate response to security incidents reduces the impact of potential breaches. The importance of having EDR integrated into ATP tools cannot be overstated, as it not only detects but also isolates compromised endpoints. It further blocks malicious activities within these endpoints, fortifying the defense of the entire network.
Multi-layered security
This security approach involves the integration of diverse security layers such as firewall protection, intrusion detection/prevention systems, antivirus solutions, behavioral analysis, anti-spyware and, sometimes, user awareness training. Each layer contributes a different aspect of security, which creates an overlapping defense that boosts the system’s capabilities in addressing a wide range of potential threats and reduces the likelihood of any successful attacks. Multi-layered security is proactive, adaptive and effective and is a must-have feature for any ATP tool.
How do I choose the best advanced threat protection software for my business?
Your choice of ATP tool should be subject to your organization’s security requirements, as there is hardly any one-size-fits-all solution to enterprise security. Above all criteria, you should go for an ATP solution that provides the coverage and functionality that match your firm’s security demands. Besides that, you should also factor in the tool’s pricing structure and be sure they offer a plan that matches your company’s budget.
Also pay particular attention to features you consider critical to your organization’s security, as some of the solutions may place greater emphasis on real-time detection and response, threat hunting and behavioral analysis, while others—especially those that target mid-sized organizations—may place more emphasis on flexible deployment, ease of use, quality support, intuitive dashboards and reporting capabilities.
Methodology
To conduct this review, I assessed each tool’s capabilities. I began with extensive market research to identify leading tools based on industry trends and user feedback. I considered key features such as real-time threat detection, deployment techniques, machine learning capabilities, ease of use and scalability. I also prioritized insights from reputable sources like Gartner, including expert reviews and vendor documentation.


