Ransomware incidents cause significant harm at many levels, including to physical and mental health; new research from U.K. security think tank Royal United Services Institute has classified this impact into three categories (Figure A):
- First-order harms: The harms to organizations and their staff. Examples include data loss, reputational harm and heart attacks.
- Second-order harms: The indirect harms to organizations and individuals. Examples include clients and customers in supply chains might be targeted, and patients’ cancer treatments are disrupted.
- Third-order harms: The harms to the wider society, economy and national security. An example includes citizens losing trust in a state’s ability to provide basic services.
Figure A
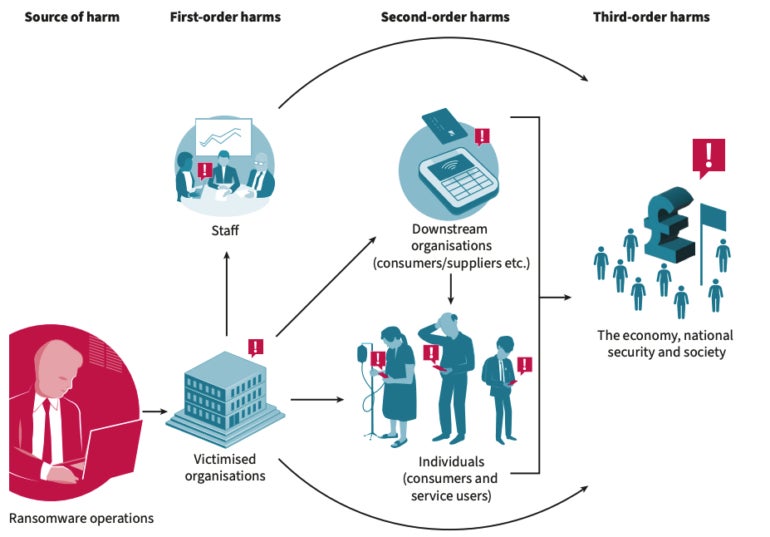
The RUSI’s research is based on interviews with victims and incident responders of ransomware attacks and reflects “new and existing types of harm to the U.K. and other countries.”
First-order harms: Direct targets of ransomware attacks
The direct targets are organizations and staff directly exposed to ransomware.
Infrastructure harm
Organizations hit by a ransomware attack may suffer physical or digital harm to data and systems. Data loss from the encryption of data by ransomware can be devastating, especially if the threat actor manages to also access the backup systems and render them useless. Thousands of computers can also become unusable for their users, forcing organizations to suddenly return to operating “by pen and paper.”
Operational Technology might also be impacted. The increasing convergence of IT and OT leave physical infrastructures more vulnerable to ransomware, even though most ransomware operators lack the capability to directly compromise OT or Industrial Control Systems; one example is when ransomware’s impact on IT prevents other systems (e.g., fire controls, doors, gates or closed circuit television) from working properly.
An organization’s incident response to ransomware might impact business because incident handlers often need to isolate parts of the IT infrastructure to conduct their remediation and recovery operations – sometimes for weeks.
SEE: NCSC Study: Generative AI May Increase Global Ransomware Threat (TechRepublic)
Financial harm
The financial harm attributed to ransomware attacks, while being very impactful for organizations, can be tricky to estimate. While the cost of a ransom payment can be measured easily, it is harder to estimate the financial loss resulting from the incident and the time it took to recover the systems, such as the missed opportunities and reduced productivity. According to the study, “many organizations generally have limited understanding of the overall financial impact a ransomware attack has on the organization, particularly with respect to financial harm that is not covered by an insurance policy, or which plays out over the long term.”
Additional costs, such as hiring external parties to help with the incident response, often far exceeds the amount for the ransom payment. Incident response teams, when externalized (e.g., lawyers and PR professionals), become very costly when incidents are complex.
Reputational harm
Reputational harm is another primary concern for organizations that fall victim to ransomware. Victims fear bad media reports and customers or clients who might consider the organization unable to provide a particular service. However, RUSI reported that some interviewees, including crisis communication experts and lawyers, indicated that “reputational harm may not be as severe as has been assumed in the literature,” yet the risk of reputational harm is much greater in case of data exfiltration or if customer services are interrupted.
Psychological and physical harm
The psychological harm of ransomware attacks on staff is intense and is often overlooked. Considerable stress for the individuals involved in responding to ransomware attacks can lead companies to hire a post traumatic stress disorder support team. Higher levels of employees suffer from stress due to financial concerns, while middle management suffers from stress caused by extremely long workdays, including particularly stressful communications with the threat actor. IT teams are the main victims, as they suffer from extreme workday conditions and feel a direct responsibility for protecting the organization’s systems. IT teams also have a very detailed understanding of the gravity of the situation from a technical point of view.
For other employees, confusion and loss of orientation can be felt because they are not familiar with technical details or do not have enough information to have a full picture of the situation.
Anger toward the attacker or anxiety/terror might also be felt from the IT staff or other employees.
In addition, staff might experience physical harm as a result of ransomware attacks; possible effects are weight changes, sleep deprivation, mental exhaustion, physical burnouts, heart attacks or stroke. One interviewee reported they knew of an IT staff member who took their own life following a ransomware incident.
Second-order harms: Indirect consequences of ransomware attacks
This category involves organizations and individuals indirectly harmed by ransomware, such as clients or customers or in the supply chain of a victim entity.
Infrastructure harm
For starters, ransomware attacks on outsourced IT sources might be harmful; cloud service providers might be attacked, and their customers might end up with their own data being lost. Manufacturing and logistics are also part of supply chains that might be targeted. In these cases, customers who cannot get their products or services on time from the victimized supplier might lose business or suffer from delays.
Reputational harm
The supply chain parties affected by ransomware also often lose their customers’ trust; those customers might decide to choose other suppliers.
Ransomware attacks might steal data from companies indirectly via their suppliers, which might result in the data being exposed publicly or sold to other cybercriminals in underground marketplaces. This all leads to reputational harm once it is known publicly.
Physical harm
Individuals’ health can be harmed by ransomware attacks. For example, ransomware attacks in some cases have forced hospitals to postpone surgeries or disrupt patients’ cancer treatments, which also causes a lot of stress and anxiety in addition to the delays. Emergency services might be diverted to other hospitals as well, impacting survivability and recovery for patients.
Financial harm
Individuals might be financially impacted; for instance, in the U.K., ransomware attacks against local authorities disrupted residents’ abilities to access housing benefits. Threat actors might try to extort money from them with data obtained from the attack. The attackers might, for example, blackmail individuals and threaten to reveal health information or other personal information about them.
The costs of goods and services for individuals might increase in reaction to the cost of the incident response and remediation for the impacted organization.
Third-order harms: Ransomware’s impact on nations and society
This last category describes the effects of ransomware activity on a country’s economy, society and national security.
National security harm
Ransomware is widely considered a threat to national security, mostly for these two reasons:
- The disruption of critical national infrastructure and strategic sectors.
- The strategic advantage that ransomware can create for hostile states.
Two examples for these threats are:
- The ransomware operations linked to the North Korean regime, which are financially motivated and aimed at generating revenue for the regime.
- The Russian-speaking ransomware attackers whose operations benefit from a safe harbor in Russia, the state maintaining close ties with cybercriminals or groups, and co-opting them or their capabilities for its own needs, according to the study.
Societal harm
There can be societal harm in reaction to ransomware attacks. For instance, citizens might lose trust in states that cannot seem to be able to protect them or provide basic services at any time, especially when it is related to healthcare.
The disruption of specific organizations that are mandatory for nations has the potential to cause huge economic harm that can have an impact on entire societies.
Why is there not much feedback about ransomware harms?
Victims of ransomware attacks rarely share their experiences. In the best case, companies share an incident response report publicly to help other organizations improve their defense but also often to show their customers that they have handled the threat in a responsive way, yet a lot of organizations stay silent for various reasons: reputational concerns, fear or legal reasons.
The shared incident response reports are often very technical but lack important details about harm caused other than financial details: who were the indirect victims, which can include other organizations, communities and individuals, and the wider society, and how they were affected. As stated by the RUSI in the report, “there is a real human impact to ransomware attacks that is yet to be fully grasped and measured.”
How to limit harms after a ransomware attack
Regarding infrastructure, clear incident response feedback needs to be shared amongst all staff involved in incident response to help increase efficiency if another ransomware attack hits the company later. The feedback should include details of the technical incident response as well as describe what failed and what worked.
Organizations should help staff that are highly involved in ransomware incident response and might suffer from PTSD by offering them the possibility to consult medical or psychological experts.
Incident response exercises should be done on a regular basis to train incident responders to improve against this threat and lessen the stress they might feel when a ransomware incident hits the company.
How to prevent ransomware attacks
Organizations should always back up their important data on external devices or secure cloud services and ensure the data is only accessible by authorized staff.
Security solutions based on endpoint behavior must be used in order to detect early signs of ransomware activity, such as the sudden massive modification of filenames.
All operating systems, software and firmware must always be kept up to date and patched to avoid being compromised by a common vulnerability.
Network segmentation should be used when possible to reduce the chances of the entire network being affected by ransomware.
Conclusion
Ransomware attacks and their impacts are well understood from a technical point of view, yet it is difficult to estimate the costs to recover from those attacks and even more difficult to estimate all the impact they have on nations, organizations, staff and individuals. The psychological impact of ransomware attacks in particular is largely overlooked and should be taken into much more consideration.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.


