The internet is a difficult space for Australian small and midsize businesses at the moment. Not only does the rate of innovation challenge them to adopt disruptive new technologies with minimal resources, but they also have to contend with the same cyber threats as all other businesses. Then, those that are breached are likely to subsequently fail, with 60% of SMBs closing after being breached.
And the regulators are deeply concerned.
A recent report by ASIC found that “medium and large” organisations consistently reported more mature cyber security capabilities than small organisations, which lagged behind in most critical areas: supply chain risk management, data security and consequence management.
In response to the threats, the Australian government announced an AU $20 million package to support small businesses. This includes the establishment of a voluntary cyber “health check” program to help small business owners better understand their cyber security maturity. Additionally, $11 million of the package will go to a Small Business Cyber Resilience Service, which will provide a one-on-one service to help small businesses recover from a cyber attack.
These efforts target the areas where SMBs are at their weakest. Nonetheless, in the face of rising cyber threats, small businesses will also need to take it on themselves to focus far more on resilience than they have been.
Jump to:
- The risk in numbers
- The cost to small business
- What can small businesses do?
- Start with the essential 8
- Every SMB needs a crisis management plan
The risk in numbers
In some areas, such as their ability to detect threats and recover from them, the ASIC data shows that small businesses are only marginally better than half as effective as their medium and large counterparts (Figure A).
Figure A
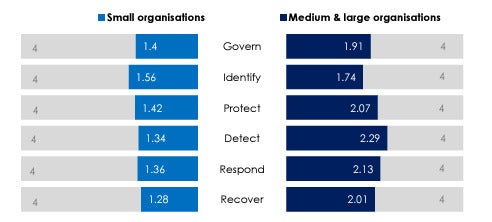
Overall, a significant percentage of small businesses:
- Do not follow or benchmark against any cyber security standard (34%).
- Do not perform risk assessments of third parties and vendors (44%).
- Have no or limited capability in using multi-factor authentication (33%).
- Do not patch applications (41%).
- Do not perform vulnerability scans (45%).
- Do not have backups in place (30%).
These weaknesses mean that small businesses remain at great risk at relatively basic and otherwise manageable cyber threats, including phishing, ransomware and business email compromise.
The cost to small businesses
Separately, the Australian Signals Directorate published its Annual Cyber Threat Report 2022-2023. The report found that the average cost of cyber crime had increased by 14% in the past year. The cost to small businesses was $46,000, while to medium businesses it was $97,200, and to larger enterprises it was $71,600 (Figure B).
Figure B
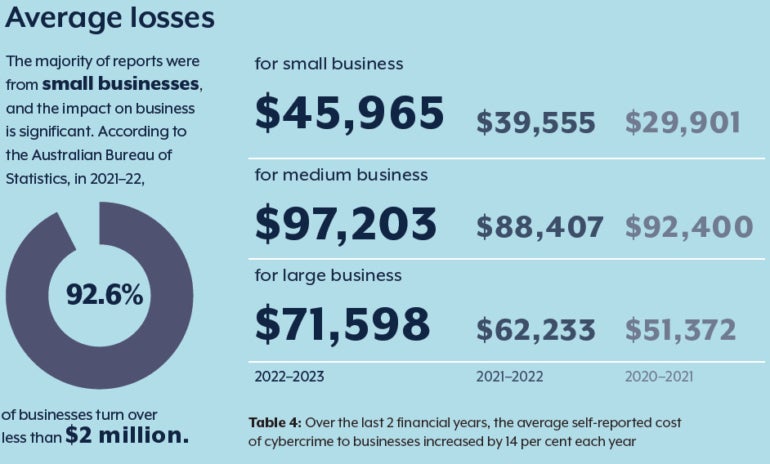
That is a cost burden on every enterprise, of course, but for SMBs it seems to be particularly destructive. Around 60% of small businesses that do suffer a breach go out of business as a direct consequence of that.
In other words, cyber security is a genuine existential threat to these businesses. Even those that do survive the direct cost of the breach need to contend with the reputational damage, which can lose it customers and partners and affect short-term cash flow. In a best-case scenario, a cyber breach “just” inhibits the small business’s ability to scale and grow.
A lack of resources a critical challenge in protecting SMEs
Small businesses will have small IT teams — or, more likely, a single IT professional on staff — and their role is generalist in nature. They’ll be responsible for setting up IT security, but they’ll also be managing the servers and website, as well as maintaining cloud environments and device fleets among other tasks. They’re not going to be able to dedicate significant amounts of their time to specific cyber security projects.
SEE: Australian nonprofits face cyber risk due to limited resources.
Even if they did, they wouldn’t have much to invest. Close to half of Australian small businesses (48%) spend less than $500 on cyber security per year.
For the overworked and exhausted IT professional in an SMB, the goal needs to be to establish a best practices approach to cyber security that will neither be difficult to maintain, nor require specialised resources. The new government resources announced can help with that, but there’s a lot that SMBs can do independent of that government support to get started immediately.
Small businesses should start with the ‘Essential Eight’
In recognising the limitations with what small businesses can access, the ASD and Australian Cyber Security Centre pulled together the Essential Eight — a series of best practice recommendations for security and small businesses. These are:
- Creating, implementing and managing a whitelist of approved applications.
- Implementing a process to regularly update and patch systems, software and applications.
- Disabling macros in Microsoft Office applications unless specifically required, and training employees not to enable macros in unsolicited email attachments or documents.
- Hardening user applications by ensuring web browsers are configured securely to block malicious content. Only using necessary browser extensions and keeping them updated.
- Restricting administrative privileges to those who need them.
- Setting up automatic updates for patching operating systems.
- Using strong, unique passwords and enabling multi-factor authentication.
- Conducting daily backups of critical data and isolating backups from your network.
While these might all seem straightforward enough, to many of the employees within small businesses, where there aren’t typically policies in place to govern best practice use of the technology, there is the need for ongoing training and vigilance from the IT function to ensure the entire organisation remains in compliance.
Equally, the investment required across these is minimal and doesn’t require the small business to take on any additional security software or solutions.
Every SMB needs a crisis management plan
In addition to implementing the Essential Eight, the IT pro or pros working in the small business should take it on themselves to come up with a response strategy in the event that there is a breach.
SEE: Explore these six steps to a successful incident response plan.
This is something even the largest of enterprises overlook to their detriment. For example, when telecommunications giant, Optus, recently experienced a total outage, one of the biggest concerns people had was the lack of communication and response. As it turned out, this was due to a lack of a crisis management plan.
IT professionals working at small businesses need to come to terms with the reality that their businesses are vulnerable. As understaffed and under-budget as many of them are, a breach is likely at some point. Having a comprehensive crisis management plan is critical for mitigating both the cost and damage done by the breach; and, in doing so, they will help their organisation be one of the majority that can recover from an incident.


